
Ultra secure, Data Privacy and Secure Storage

Google Image Search With Image Test
 Google thinks that the images are similar. Obviously it didn't recognize the fish or the coral reef or the fact that it was an underwater picture. Some of the results returned were of a flower, art, desserts and multi-colored mosaic things.
Google thinks that the images are similar. Obviously it didn't recognize the fish or the coral reef or the fact that it was an underwater picture. Some of the results returned were of a flower, art, desserts and multi-colored mosaic things. I then renamed it to something silly so that the name of the pic wouldn't give any clues. Google knew that it was Albert Einstein right away. They probably developed the algorithm using famous people and Einstein is one of them.
I then renamed it to something silly so that the name of the pic wouldn't give any clues. Google knew that it was Albert Einstein right away. They probably developed the algorithm using famous people and Einstein is one of them.

RugbyMetrics Queries
 I have been getting some queries via comment postings about RugbyMetrics. Some people have even been trying to find a trial download. I will be posting some sample results and white papers here shortly. In the meantime, if you have any queries, please drop me a line at:
I have been getting some queries via comment postings about RugbyMetrics. Some people have even been trying to find a trial download. I will be posting some sample results and white papers here shortly. In the meantime, if you have any queries, please drop me a line at:Who Was At The Computer -- Solving a Whodunnit
 I was idly watching some of the Casey Anthony murder trial being streamed on the Internet. She is charged with brutally disposing of her bothersome two-year-old child who was impinging on her party life.
I was idly watching some of the Casey Anthony murder trial being streamed on the Internet. She is charged with brutally disposing of her bothersome two-year-old child who was impinging on her party life.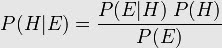
- H represents a specific hypothesis, which may or may not be some null hypothesis.
- E represents the evidence that has been observed.
- P(H) is called the prior probability of H that was inferred before new evidence became available.
- P(E | H) is called the conditional probability of seeing the evidence E if the hypothesis H happens to be true. It is also called a likelihood function when it is considered as a function of H for fixed E.
- P(E) is called the marginal probability of E: the a priori probability of witnessing the new evidence E under all possible hypotheses.
A Standard For Twitter Hashtags
 I follow Bath Rugby players on Twitter, among other things. I notice that some of the team are avid users of Twitter. They are also quite inventive with hashtags. Hashtags are much more than search tools. They can be cleverly used to create innuendo, a wry comment, a joke, or a commentary all under the guise of just being a hashtag.
I follow Bath Rugby players on Twitter, among other things. I notice that some of the team are avid users of Twitter. They are also quite inventive with hashtags. Hashtags are much more than search tools. They can be cleverly used to create innuendo, a wry comment, a joke, or a commentary all under the guise of just being a hashtag.Lately Skype is a piece of Crap -- Skype virus???
 I am having serious issues with Skype. I travel back and forth between the tropics, and I have an XP desktop in the tropics. Until a day before yesterday (June 14, 2011), the platform was quite stable. I was using Skype with a cheap webcam with no issues.
I am having serious issues with Skype. I travel back and forth between the tropics, and I have an XP desktop in the tropics. Until a day before yesterday (June 14, 2011), the platform was quite stable. I was using Skype with a cheap webcam with no issues.Want a Software Job? Finish This Test .... Part 3

Want a Software Job? Finish This Test .... Part 2
 In yesterday's blog entry, I detailed a new paradigm where developers and coders who applied for a job, were sent back a programming test by email, without any personal contact at all. One developer that I know, took umbrage to the system and sent back the following response:
In yesterday's blog entry, I detailed a new paradigm where developers and coders who applied for a job, were sent back a programming test by email, without any personal contact at all. One developer that I know, took umbrage to the system and sent back the following response:Want a Software Job? Finish This Test .... Part 1
 There is a relatively new paradigm for hiring software developers and coders. It consists of an applicant sending in his resume online. Before there is any initial contact at all, the applicant is sent a coding exercise. Reprinted below is one such:
There is a relatively new paradigm for hiring software developers and coders. It consists of an applicant sending in his resume online. Before there is any initial contact at all, the applicant is sent a coding exercise. Reprinted below is one such:We have reviewed your resume and would like to move forward in our interview process with you! In order for us to understand how you approach your work and to move to the next level of our process, please complete the following coding exercise.
Using Java/Python, please design and implement the classes for a card game (pick any game, Poker for example), which uses an ordered deck of cards, containing 52 cards divided in 13 ranks (A, 2, 3, 4, 5, 6, 7, 8, 9, 10, J, Q, K) with four suits: spades, hearts, diamonds and clubs. The cards can be, at a minimum, shuffled, cut, and dealt (feel free to implement additional ones that are required by the game).
* You do not have to model the gameplay, but include code required for the different stages of the game (e.g., evaluating player hands)
* You do not have to model any player bidding
* List any assumptions you make
Thanks again for your help in streamlining this process and we look forward to reviewing your code!
Crime-Solving Website for Mothers Who Kill Their Children
 The news tonight (or I guess that it is morning now) is full of news of mothers or step mothers who kill children and dump the bodies.
The news tonight (or I guess that it is morning now) is full of news of mothers or step mothers who kill children and dump the bodies.And then we have the case of Julianne McCrery who drove from Texas with her six year old gifted boy, Camden Hughes and killed him in the North. He was found under a blanket May 14 alongside a remote road in South Berwick, Maine, near the New Hampshire border, sparking a massive tri-state manhunt.