
Notes to self: If you get this error on your javascript console:
"Uncaught SyntaxError: Unexpected token ILLEGAL"
The first thing to try, is that if you are passing a string as a parameter, put it single quotes.
This drained me for an hour.
 It looks like Microsoft is desperate for developers to make apps for the Mango phone. I am a registered Microsoft developer, and I just received the email printed below. (They want $99 from me to develop apps. Amazon just waived the $99 fee for developers to develop on the Android phone). Here is the email:
It looks like Microsoft is desperate for developers to make apps for the Mango phone. I am a registered Microsoft developer, and I just received the email printed below. (They want $99 from me to develop apps. Amazon just waived the $99 fee for developers to develop on the Android phone). Here is the email: When programming in Java, I like java.util.GregorianCalendar a lot. It makes date and time manipulation easy peasy. For example, I have an application where I have to get the current datetime and add twenty minutes. It happens in a couple of lines:
When programming in Java, I like java.util.GregorianCalendar a lot. It makes date and time manipulation easy peasy. For example, I have an application where I have to get the current datetime and add twenty minutes. It happens in a couple of lines: One of the reasons that computer gaming is so popular and addictive, is that it offers some real excitement in the boring moments of a person's life. If one has a normal life, it can get pretty mundane. Playing a computer game stimulates the production of brain chemicals like dopamine and other endorphins like adrenaline. One can get used to the chemical rush produced by playing video games.
One of the reasons that computer gaming is so popular and addictive, is that it offers some real excitement in the boring moments of a person's life. If one has a normal life, it can get pretty mundane. Playing a computer game stimulates the production of brain chemicals like dopamine and other endorphins like adrenaline. One can get used to the chemical rush produced by playing video games. I just spent several hours pulling out my hair trying to escape the ampersand character in an .aspx URL with parameters. The URL was a third party URL which needed to be encoded. I was working in JSP, JavaScript, XHTML, JSF, and JSTL.
I just spent several hours pulling out my hair trying to escape the ampersand character in an .aspx URL with parameters. The URL was a third party URL which needed to be encoded. I was working in JSP, JavaScript, XHTML, JSF, and JSTL. 

 I am a registered Nokia Mobile Developer. I got this email from them late last night informing me that my information has been compromised:
I am a registered Nokia Mobile Developer. I got this email from them late last night informing me that my information has been compromised: I was deep in conversation with a tech-savvy epidemiologist at a dinner party. He is a physician who is the head of an NGO (non-government organization) with offices in various countries on a few continents. He happened to mention that he had over a million record sets that needed data-mining in a very specific way.
I was deep in conversation with a tech-savvy epidemiologist at a dinner party. He is a physician who is the head of an NGO (non-government organization) with offices in various countries on a few continents. He happened to mention that he had over a million record sets that needed data-mining in a very specific way.
 I am starting to get a little ticked off at how much data is being collected on me when I surf the internet. Websites often ask for authentication data including name and birth date, which they match to an IP address and can get a geographic location. For websites that I deem do not need that information, I always give them an alias, fake birthday and I use a throw-away free email address.
I am starting to get a little ticked off at how much data is being collected on me when I surf the internet. Websites often ask for authentication data including name and birth date, which they match to an IP address and can get a geographic location. For websites that I deem do not need that information, I always give them an alias, fake birthday and I use a throw-away free email address.

 The entry below on the putative consciousness of Google got me to thinking about "The Semantic Web". It was/is an initiative of W3C to make all web pages machine readable.
The entry below on the putative consciousness of Google got me to thinking about "The Semantic Web". It was/is an initiative of W3C to make all web pages machine readable. I just had an amazing epiphany on how Google Adsense and Google advertising works, and I can't say that I am thrilled. Google reads my browsing history to serve up ads to me. I am not sure that I like that!
I just had an amazing epiphany on how Google Adsense and Google advertising works, and I can't say that I am thrilled. Google reads my browsing history to serve up ads to me. I am not sure that I like that! In a previous blog post, I predicted the eventual demise of Facebook. This article further explains why I think that.
In a previous blog post, I predicted the eventual demise of Facebook. This article further explains why I think that. A couple of years ago, it would have been heresy to say that MySpace was irrelevant.
A couple of years ago, it would have been heresy to say that MySpace was irrelevant. It is now a ghost of what it was, and it IS irrelevant. Facebook has moved in and trounced it. However, I will posit that Facebook is dead man walking and they don't know it.
It is now a ghost of what it was, and it IS irrelevant. Facebook has moved in and trounced it. However, I will posit that Facebook is dead man walking and they don't know it.
 Google thinks that the images are similar. Obviously it didn't recognize the fish or the coral reef or the fact that it was an underwater picture. Some of the results returned were of a flower, art, desserts and multi-colored mosaic things.
Google thinks that the images are similar. Obviously it didn't recognize the fish or the coral reef or the fact that it was an underwater picture. Some of the results returned were of a flower, art, desserts and multi-colored mosaic things. I then renamed it to something silly so that the name of the pic wouldn't give any clues. Google knew that it was Albert Einstein right away. They probably developed the algorithm using famous people and Einstein is one of them.
I then renamed it to something silly so that the name of the pic wouldn't give any clues. Google knew that it was Albert Einstein right away. They probably developed the algorithm using famous people and Einstein is one of them.

 I have been getting some queries via comment postings about RugbyMetrics. Some people have even been trying to find a trial download. I will be posting some sample results and white papers here shortly. In the meantime, if you have any queries, please drop me a line at:
I have been getting some queries via comment postings about RugbyMetrics. Some people have even been trying to find a trial download. I will be posting some sample results and white papers here shortly. In the meantime, if you have any queries, please drop me a line at: I was idly watching some of the Casey Anthony murder trial being streamed on the Internet. She is charged with brutally disposing of her bothersome two-year-old child who was impinging on her party life.
I was idly watching some of the Casey Anthony murder trial being streamed on the Internet. She is charged with brutally disposing of her bothersome two-year-old child who was impinging on her party life.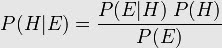
 I follow Bath Rugby players on Twitter, among other things. I notice that some of the team are avid users of Twitter. They are also quite inventive with hashtags. Hashtags are much more than search tools. They can be cleverly used to create innuendo, a wry comment, a joke, or a commentary all under the guise of just being a hashtag.
I follow Bath Rugby players on Twitter, among other things. I notice that some of the team are avid users of Twitter. They are also quite inventive with hashtags. Hashtags are much more than search tools. They can be cleverly used to create innuendo, a wry comment, a joke, or a commentary all under the guise of just being a hashtag. I am having serious issues with Skype. I travel back and forth between the tropics, and I have an XP desktop in the tropics. Until a day before yesterday (June 14, 2011), the platform was quite stable. I was using Skype with a cheap webcam with no issues.
I am having serious issues with Skype. I travel back and forth between the tropics, and I have an XP desktop in the tropics. Until a day before yesterday (June 14, 2011), the platform was quite stable. I was using Skype with a cheap webcam with no issues.
 In yesterday's blog entry, I detailed a new paradigm where developers and coders who applied for a job, were sent back a programming test by email, without any personal contact at all. One developer that I know, took umbrage to the system and sent back the following response:
In yesterday's blog entry, I detailed a new paradigm where developers and coders who applied for a job, were sent back a programming test by email, without any personal contact at all. One developer that I know, took umbrage to the system and sent back the following response: There is a relatively new paradigm for hiring software developers and coders. It consists of an applicant sending in his resume online. Before there is any initial contact at all, the applicant is sent a coding exercise. Reprinted below is one such:
There is a relatively new paradigm for hiring software developers and coders. It consists of an applicant sending in his resume online. Before there is any initial contact at all, the applicant is sent a coding exercise. Reprinted below is one such:We have reviewed your resume and would like to move forward in our interview process with you! In order for us to understand how you approach your work and to move to the next level of our process, please complete the following coding exercise.
Using Java/Python, please design and implement the classes for a card game (pick any game, Poker for example), which uses an ordered deck of cards, containing 52 cards divided in 13 ranks (A, 2, 3, 4, 5, 6, 7, 8, 9, 10, J, Q, K) with four suits: spades, hearts, diamonds and clubs. The cards can be, at a minimum, shuffled, cut, and dealt (feel free to implement additional ones that are required by the game).
* You do not have to model the gameplay, but include code required for the different stages of the game (e.g., evaluating player hands)
* You do not have to model any player bidding
* List any assumptions you make
Thanks again for your help in streamlining this process and we look forward to reviewing your code!
 The news tonight (or I guess that it is morning now) is full of news of mothers or step mothers who kill children and dump the bodies.
The news tonight (or I guess that it is morning now) is full of news of mothers or step mothers who kill children and dump the bodies.